With most businesses now supporting the majority of their workforce from home, it requires that organizations use the tools and solutions that allow and empower their business to support the remote workforce effectively and securely. Praim’s solutions including the updated ThinMan Server, ThinOX and Agile products allows businesses to easily and seamlessly support the remote workforce who make use of managed solutions (either thin clients, laptops or personal computers) for accessing business-critical resources.
With little effort, your business can stand up a ThinMan Server in the cloud, install a trusted certificate and connect devices to ThinMan in only a few steps. In this walkthrough, we will take a look at just how easy it is to provision your Praim infrastructure in the cloud and support the remote workforce with centralized management and administration of endpoints.
Recent Praim Updates Streamline the Process
Praim has drastically simplified the steps required to provision end user clients with Praim solutions with recent updates to the product portfolio. With ThinMan Server 8.0 and higher, a new connectivity architecture was introduced called Web Socket Secure. What is this?
With the new web socket secure architecture, the number of network ports that are required for communicating back to the ThinMan Server is reduced down to only needing TCP port 443. This helps to greatly simplify the management configuration of the network connections that are needed for remote workers.
When managing remote workers who are working from home, administrators have to deal with the wide range of home networks that exist for remote employees. End users may not have the technical skills needed to troubleshoot network connectivity or provision the network requirements needed for connecting back to thin client infrastructure.
Reducing the connectivity requirement down to TCP port 443 helps to ensure that connectivity can be easily established between remote work environments at home and the corporate infrastructure using Praim solutions since TCP port 443 is generally a default outbound port that is open on most networks.
This simplification provides the connectivity needed to give your organization the flexibility to stand up a ThinMan Server anywhere, including the cloud and managing end user environments, even in home networks.
Deploying ThinMan in Azure
Let’s take a look at the example of deploying a ThinMan Server in Azure. This is as simple as deploying a Windows Server in Azure and then installing the ThinMan Server installation. First, let’s deploy a Windows Server in our Azure environment.
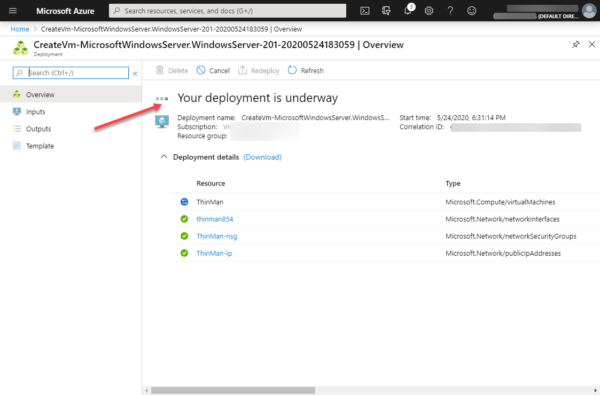
Deploying a Windows Server VM in Microsoft Azure as a ThinMan host
Once you have a virtual machine provisioned in Azure, it is as simple as installing the ThinMan Server on the virtual machine. Note the ports that are configured by default. With secure SSL traffic, this is port 443.

Installing ThinMan Server on an Azure virtual machine
With a simple “next, next, finish” installer, ThinMan Server is installed quickly and easily.

ThinMan Server is successfully installed on the Azure virtual machine
With Microsoft Azure, you have to add ports in the “network security group” configuration for the virtual machine for allowing ingress traffic into the virtual machine. This is a simple process with ThinMan Server since we only have to allow port 443 inbound for connections from clients. This also streamlines the management of network security group inbound rules for your ThinMan Server.
As mentioned earlier, this makes things extremely simple and straightforward from the client connection side since there is only a single port that needs opened for outbound traffic. Below, we are adding the required TCP port 443 inbound to the ThinMan Server in the Azure IaaS environment. This is found in Networking > Inbound port rules of the Azure virtual machine properties.

Adding the required Azure network security group inbound port rule for communicating with ThinMan
Adding end user clients to ThinMan Server housed in Azure
Once the inbound rule is in place for your ThinMan Azure virtual machine, end user clients can now successfully connect to the ThinMan Server hosted in Azure.
While installing Agile on the device, in order to activate the product, the user will be requested to insert the ThinMan address.

As you can see below, hitting the ThinMan Server with the Azure-assigned public IP address is successful.

Client successfully connects to the Azure-hosted ThinMan Server
Once you test the server connection to the ThinMan Server, you will see the client device register with the ThinMan Server as seen below.

After testing the connection to the ThinMan Server, the end user client is registered with the ThinMan Server
Once the end user client is registered with the ThinMan Server, you can perform all the common management actions to control the endpoint from ThinMan Server including:
- Remote assistance
- Updating
- Power functions
- Special functions and Commands
- Planned Activity
- …others (such as Offline Configuration for ThinOX)
With all the end user clients, working from home, registered in a single location for administration and management, this greatly simplifies the workflow of IT operations during work-from-home business directives.

Interacting with the end user client using the ThinMan Server console
Using a custom SSL certificate to secure ThinMan Server
As most are aware, securing communications over the commonly used SSL port 443 over the Internet is accomplished using SSL certificates. By default, ThinMan Server secures the communication with your end user clients by using a self-signed SSL certificate which provisions encrypted communication by default.
However, before moving into production with your ThinMan Server housed in Azure, you will want to place an appropriate trusted certificate in place on the ThinMan Server. The security of the solution is ensured by the encrypted tunnel between your remote workers working from home and elsewhere made possible by the SSL encrypted handshake using an SSL certificate. This allows secure communications even without a VPN.
A great feature that it includes out-of-the-box is integration with “Let’s Encrypt” SSL certificates. Let’s Encrypt certificates are freely available certificates that allow securing SSL communication between your server and clients via a properly signed certificate. ThinMan makes the configuration of a trusted SSL certificate extremely easy via the Endpoint Security Communication configuration.
Let’s take a look at the steps involved to provision a custom SSL certificate via the Let’s Encrypt integration in ThinMan Server. To launch the SSL configuration, navigate to Tools > Endpoint Security Communication.

Launch the Endpoint Security Communication configuration in ThinMan Server
There are two options for setting the certificate for ThinMan’s SSL communication with endpoints.
- Let’s Encrypt Certificate Manager – This makes use of the Let’s Encrypt manager built into the ThinMan Server offering for free provisioning of proper SSL certificates
- Import your Company Certificate – If you have a company-defined, trusted certificate authority that you already use for keying your organization’s trusted SSL certificates, this option allows importing a certificate from a trusted CA
Below, we are using the Let’s Encrypt Certificate Manager option.

ThinMan supports using the Let’s Encrypt certificate manager for SSL certificate generation
Enter the FQDN of the ThinMan Server for generating an SSL certificate to apply using Let’s Encrypt.

Entering the FQDN using the built-in Let’s Encrypt manager

Certificate is verified using the Let’s Encrypt certificate manager
Integrate Azure AD for authentication
With ThinMan USER+ Feature Pack, in addition to other features, your end users’ can continue authenticate with their corporate credentials even remotely and get a customized profile. ThinMan, in fact, allows you to integrate via LDAPS with your ActiveDirectory.
Depending on your organization’s authentication configuration and strategy you can adopt a “fully cloud” or mixed approach.
If the AD instance is deployed within your virtual infrastructure ThinMan enables the passthrough of credentials to the VDI. Otherwise ThinMan can also leverage Microsoft Azure AD for authentication purposes.
Many organizations are already leveraging Azure AD as part of their migration to Office 365 Software-as-a-Service (SaaS) environment.
If you make use of Azure AD, this will help to centralize the authentication model that is used by your work from home end user clients as well as for the purposes of managing your end user clients using ThinMan Server housed in the cloud. You can easily join your ThinMan Server to the Azure AD managed domain service and have access to your authentication store that is already in place.
While we won’t go through the steps here to show this process, take a look at the quick tutorial of how to join a Windows Server VM to a managed domain here.

Azure AD managed domain services allow easily integrating a cloud ThinMan Server for centralized identity and authentication
Wrapping Up
As your organization continues to leverage remote workers working from home or elsewhere, there can certainly be challenges with centralized management, administration, and security. With Praim ThinMan Server housed in the cloud leveraging the new web socket secure protocol, you can easily connect your end user clients to your ThinMan Server housed in the cloud with little to no network reconfiguration.
As shown, it is a simple process to install ThinMan on an Azure IaaS VM, add the appropriate inbound network rule, add an end user client machine such as Agile4PC or ThinOX4PC, manage the certificates on the ThinMan Server, and even integrate your installation with Azure AD.
Praim’s updated portfolio of great products that easily facilitate remote workers make the configuration extremely painless, whether you are on-premises or in the cloud.
Be sure to check out Praim ThinMan Server for a fully-featured trial version to test in your environment here.







